
What is Smishing? Learn How to Recognize SMS Cyberattacks
October 20, 2020
Phishing smishing
Smishing attacks are steadily on the rise. Here’s what you need to know.
Part of cyber safety is recognizing an attack when you see one, and the other part of staying safe from smishing is taking time to look at a smishing example. Recognizing a real-world message as smishing by having seen a similar smishing example before, is a fast path to staying safe. Just like email got more dangerous when phishing became commonplace, text messaging became more dangerous when smishing became a thing.
In this post, we’ll explore what smishing is and what to look out for to keep your information safe.
In this post, we’ll explore what smishing is, and what to look out for to keep your information safe. Feel free to also explore our more detailed post on this topic, where we look at 7 Suspicious Signs of Danger when you are evaluating the safety of a text message.
What is Smishing?
Phishing is “the fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.” Smishing, therefore, is the same fraudulent practice with the same attempted goal, but done over text message, or SMS (short message service).
Businesses are increasingly becoming more vulnerable to smishing, especially since BYOD has become commonplace, especially with so many employees working remotely from home networks or other public spaces. Any compromise of their devices could aid hackers in infiltrating your business.
We know smishing is on the rise for many reasons. Anecdotally, our clients tell us about smishing attacks that they've experienced. Statistically, we know from Google Trends data (searches for Smishing Example) that there is a heightened interested and concern, as well:
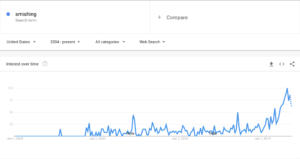
Smishing is significantly less common than phishing (for now?), per Google Trends data. But that could easily change. Other statistics suggest the number of smishing attacks rose by a whopping 700% in the first six months of 2021.
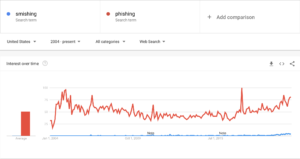
And that's exactly why you should be concerned: most of us are far more attuned to identifying a fraudulent phishing email, than we are to identifying a smishing attack. Now is the time to change that, by looking at smishing examples to help you develop a level of pattern recognition to know when a message seems unsafe.
And that's exactly why you should be concerned: most of us are far more attuned to identifying a fraudulent phishing email, than we are to identifying a smishing attack. At this time, fewer than a mere 35% of people even know what a smishing attack is – and this figure includes Millennials and Gen Z’ers between the ages of 23 and 38 – a group that is pretty tech savvy. Now is the time to change that, by looking at smishing examples to help you develop a level of pattern recognition to know when a message seems unsafe.
Related reading: 7 Suspicious Signs of Danger when you are evaluating the safety of a text message.
What Does a Smishing Attack Put at Risk?
Simply put—your personal data and information. And further, your company’s data is at risk, as your phone likely stores sensitive company info as well. In many circumstances, smishermen will use the stolen data to make a profit. For example, trying to access your financial accounts by luring you to log in to a fake version of your banking website.
Other smishing attacks attempt to get you to disclose confidential information or credentials for non-financial purposes. However, whatever the smisherman is attempting, the most common mechanisms that they will use in their smishing message, are as follows:
Malware Clickthrough: A smishing attack will prompt you to download a seemingly legitimate app, which could open your information (personal and company) up to the attackers.
Link to a Fake Site: Clicking on a link may take you to a fake site, encouraging you to input personal information.
Spoofing Local Phone Numbers: Hackers from other regions, including internationally, often track metadata and use local phone numbers to try to trick victims via texts into thinking someone they know is sending them information.
Spoofing Known Contacts: Threat actors are also getting savvy at spoofing contacts’ phone numbers to trick people into handing over personally identifiable information (PII) through a text message.
Additionally, it’s not just the standard texting apps being exploited by the bad guys, other apps including Messenger, WhatsApp, and Signal, are also being targeted with fake update notifications coming through SMS.
Smishing Example: Here are a Few to Look Out For
An increasing number of smishing attacks are simulating companies we do everyday business with which might catch us off-guard. For example, parcel delivery is a common ruse – 67% of smishing attempts involve a parcel or package delivery. Other common smishing examples include bank notifications, act-now coupons, mobile phone companies, and a variety of urgent warnings.
If you receive any of these from unknown numbers, be suspicious, especially for financial texts. Call your bank or credit card company if you have any doubt. There’s no fancy research we pulled to get these images—I just looked through my phone and asked colleagues to do the same. Here’s what we pulled:
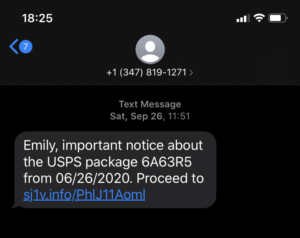
This smishing example masquerades as a package tracking update. Aside from my colleague not being named Emily, this is formatted like most SMS tracking updates, making it all the more dangerous. Here’s a tip: Look at the URL. If it doesn’t look legitimate, don’t take a chance.
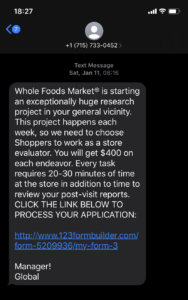
Once again—look at the URL. If this was truly a Whole Foods Market event, the URL would have “WholeFoods” in it.
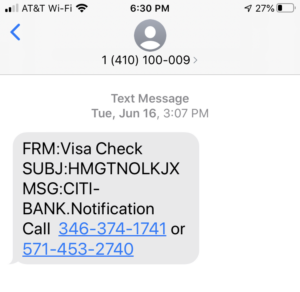
When the subject line is full of random letters, it is a smishing attack. Don’t call these numbers.
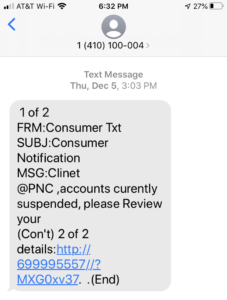
Legitimate text messages should be formatted correctly, not looking like an odd email with poor grammar.
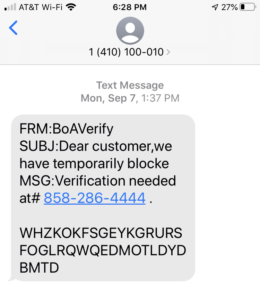
“WHZKOKFSGEYKGRURSFOGLRQWQEDMOTILDYDMBTD” isn’t a word. Don’t call that number.
WHAT TO DO IF YOU RECEIVE A SMISHING ATTACK
In addition to package delivery and financial ruses, other top scams to look out for in 2022 include debt scams, tax refund scams, reactivation scams, and family emergency scams. Here's a quick list on what to do if you receive a smishing text:
- Don’t click the link. Don’t call the number.
- Seriously. Don’t click the link. Don’t call the number.
- If you’re unsure if it’s an attack, look up the sending number online to find its legitimacy.
- Don’t respond to the SMS.
- Report the attack to the FCC to try to protect others.
- Block the number on your phone.
- Delete the text so you accidentally don’t open the link later.
- Once more for good luck: Don’t click the link. Don’t call the number.
Be safe out there—keep your data and your company information protected from smishing attacks! The more you and your employees understand what smishing and other attacks are and the damage these exploits can cause, the better you can prevent your business from falling victims to the smishermen. A little knowledge can go a long way.
If you’d like to learn more about how to protect your company’s data, try Havoc Shield’s free trial.