
When Small Business Cybersecurity Meets Bring Your Own Device (BYOD)
September 13, 2023
work from home remote device management
Maintaining small business cybersecurity while allowing BYOL (bring your own laptop) is one of the hottest topics amongst companies that seek out our help. Although there is no one-size-fits-all solution, it helps to have a contextual sense for the continuum of high risk to low risk decisions that a company can make while navigating this complex topic. Here's our shot at very simply summarizing some of the key stopovers on that continuum that we've seen companies land at.
BYOL AND Small Business Cybersecurity
BYOL (Bring Your Own Laptop), is when a company allows or requires employees to conduct company business -- work obligations -- from their personal laptop. A laptop that they've purchased on their own. On which they've likely added other programs and data associated with non-work activities. Their pictures, their personal email account, their favorite games, applications, music player, etc. And your confidential company-related data and applications. Sound like a matter that merits some intentional thought about small business cybersecurity? We think so.
The most common way that companies end up allowing BYOL is through a progression of company history that began with one or two founders starting a company from scratch, using whatever laptops they already had -- and allowing that tradition of personal laptop using to continue as other early-hires joined the team.
The Risk Continuum for BYOL
1. High Risk
The highest risk decision that you could make as an operator of a small business evaluating the possibility of allowing BYOL, is simple. It's that you allow BYOL without any additional mitigations, remediations, or compensating controls of any kind. You allow employees to use their own laptop for work, even if there is confidential information on it, and even if the employee hasn't necessarily been trained or informed of relevant company policies for handling confidential information. Sounds a high risk move for small business cybersecurity, right? It is:

2. Medium-High Risk
Moving on to slightly safer territory, suppose that you allowed BYOL, but that you predicated the use of BYOL on having employees review and acknowledge certain BYOL policies. Those policies include things like what kind of company information can and can't be stored on the laptop, acceptable use of company accounts from the laptop, and more. Furthermore, suppose that you also engage employees with modern cybersecurity training that attunes them to evolving cybersecurity risks -- things that they might encounter when they are sitting at home with their laptop, with no colleagues or IT professionals to help them second-guess a situation that arises.
You are still in the small business cybersecurity danger zone, at least in the medium-high risk category if not higher, but you've made a smart choice by engaging the team in cybersecurity, heightening their awareness about their obligations, and attuning them to emerging threats to watch out for. Here's where we're at on the continuum:

3. Medium Risk
You can do better than the previously-described efforts. If you've already involved the team positively in policies and training to keep them (and the company) safe, how about some technology enablement that benefits both them and the company? A good compromise that many teams find acceptable is to install some endpoint security -- often an antivirus package that includes malicious traffic filtering, malware detection/removal, and other helpful features. What's appealing about this, is that it benefits both the employee (personally) and the company. When the company steps up to supply this helpful protection, our experience is that employees have most often found the approach reasonable and acceptable. Even though you are asking them to install a company-managed resource on their laptop, it's one that has mutual benefit, and doesn't give the company an overbearing level of control over the employee's personally-owned laptop. Here's where we're at on the risk continuum now:
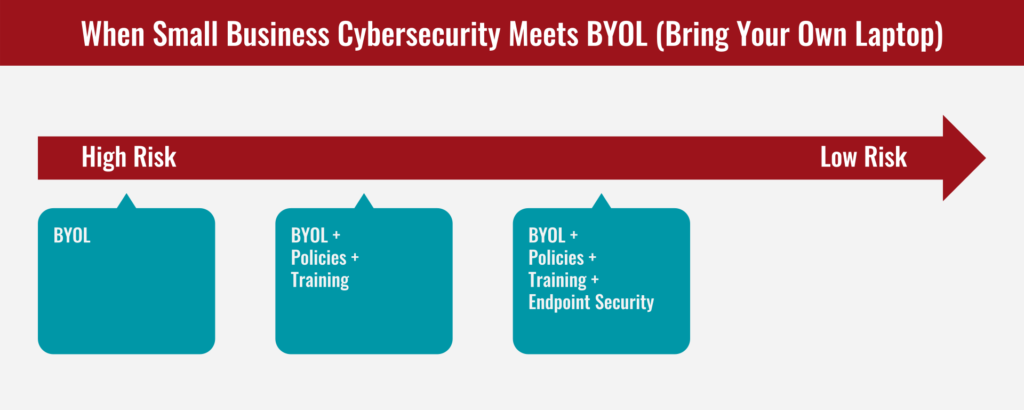
4. Low Risk
This one is the biggie. If you really want to chip away at your risk profile further, it's probably time to transition to company-owned laptops. Sure, there are some other gradations that you could possibly move to first, but there are some definite drawbacks:
- Virtual Machines: you could potentially supply virtual machines such as Amazon Workspaces that BYOL users could remotely access and conduct all of their work on. We're skeptical, however, that they'll truly isolate their work and company data/programs to that virtual environment, though. Won't they occasionally save off a document for review locally? Accidentally take a screenshot or a download that lands on their personal laptop? Get fed up with laggy internet and decide to work on their local machine? The temptations that might lead an employee off of the virtual machine are numerous.
- Device Management on BYOL: you could potentially ask employees to allow the company to install a device management agent on their personally-owned laptop. Don't expect a warm reception, though. When employees who are supplying their own laptop for work are asked to install an agent that has diagnostic inspection capabilities (things like monitoring which programs are running), and features like "remote lock" and "remote wipe", you can bet that the proposal will be a tough sell. Candidly, it's a sell we don't recommend.
So, here we are. Moving rightward on the risk continuum towards Low Risk, talking about rolling out company-owned laptops to employees who previously operated on a BYOL approach. The moment of this particular transition could certainly result in feedback from employees who "just want to keep going" with their own laptop. But with confidential information at stake in a world where the cyber threat landscape is more complex by the day, it's hard to craft a path to a low risk approach when the endpoints where all of the company's work occurs... is, well, on laptops that the company doesn't manage. Thus, we're here:
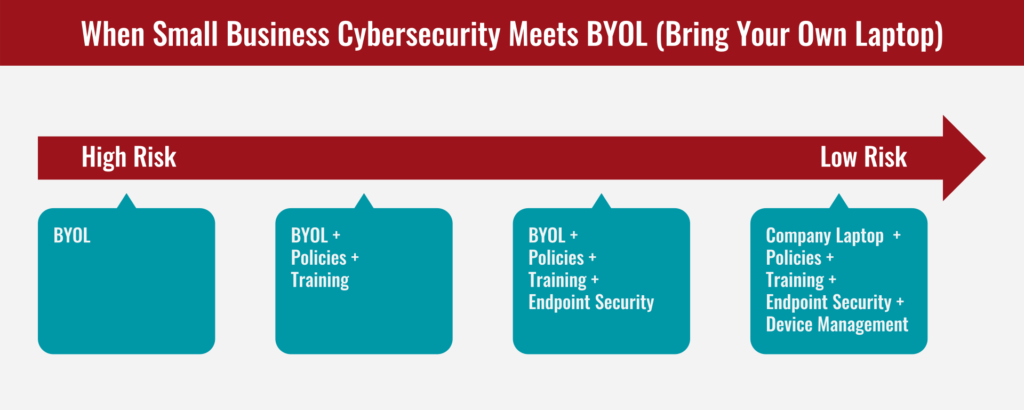
Small Business Cybersecurity & BYOL: Wrapping Up
We don't claim that we've covered all possible gradations of risk that can occur with BYOL; just a sampling of realistic situations that we've seen companies face:

Many different combinations of compensating controls can be configured to create subtle gradations in risk that aren't illustrated here. However, our point is merely to address head-on the extremes and some illustrative gradations in between, to help you start the thought process of finding the right balance for your organization. We're also eager to revisit this continuum in other BYOD areas such as smartphones, tablets, and accessories -- more on that soon.
Need help thinking it through further? Let us know.