At Havoc Shield we spend a growing portion of our time helping companies guard against increasingly complex phishing schemes. When cyber criminals take fraudulent action to pretend to be someone they aren't -- like pretending to be a representative of a bank or other trusted service provider -- they seek to extract data, financial resources, and personal information to use against you or your employees. What's worse, is that with many teams now working from home, it's harder for employees to lean over to a colleague to pose the question "does this seem legitimate". We'll help. But first, lets look at the four steps that cyber criminals use to execute a phishing attack.
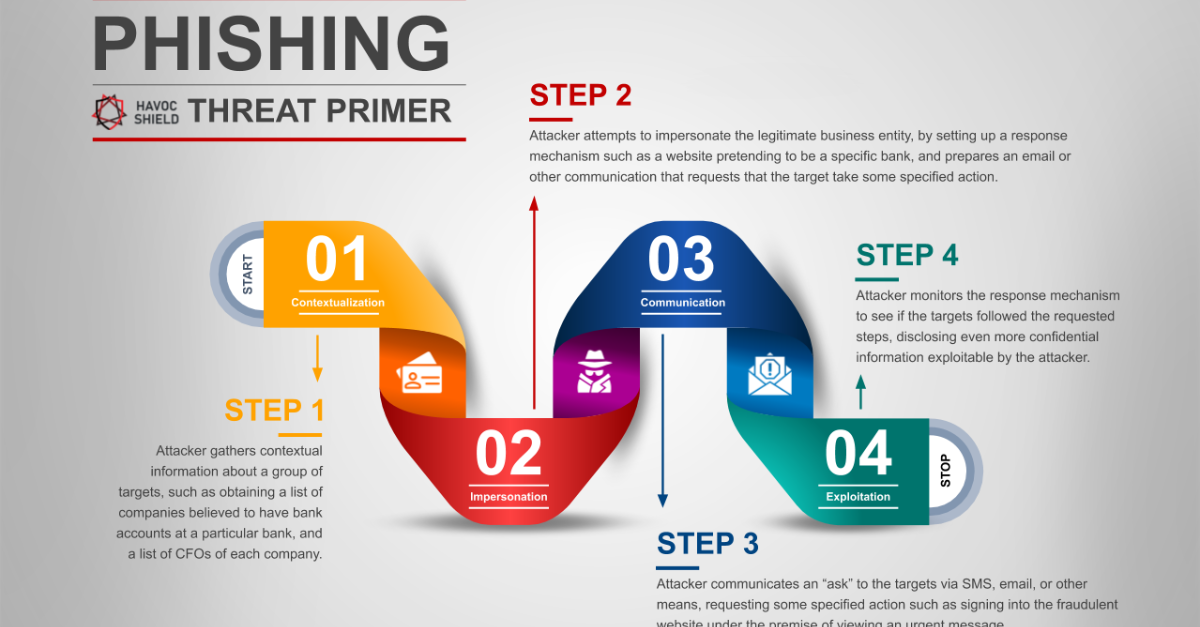
Step 1: Contextualization
Savvy cyber criminals seek to contextualize their phishing attack by using large datasets from the dark web, to learn one or two facts about their targets. For example, an attacker might have access to a list of people that are believed to be customers of a particular bank, and might also have access to a list of people that are believed to be financial decision makers at their place of work. Those lists, and especially an intersection of the two, provide cyber criminals with context that sets the stage for a phishing attack.
Step 2: Impersonation
An attacker that seeks to pretend to be an authorized representative of one of your trusted service providers (for example, your bank), will then set the stage for interacting with you in a way that they believe will persuade you that they really are an employee of the entity that they claim to be from. In a popular style of phishing attack, a cyber criminal will set up what appears to be a legitimate banking website including the logo of the bank that they believe you regularly work with. This step towards "impersonation" is all about fraudulently building credibility by appearing to be a legitimate entity that you implicitly trust.
Step 3: Communication
Cyber criminals then launch the most essential portion of their attack: they communicate with you via email, SMS, or other means, to try to engage you in further interaction. One of the simplest forms of phishing attack is to fraudulently alert you that there is a message waiting for you in your online banking portal, and to provide a link to the fraudulent site that they have prepared to resemble a legitimate banking website. They hope you'll fall for it.
Step 4: Exploitation
Because attackers often send out large batches of phishing communication, once they have sent their message impersonating one of your trusted service providers, they hope that you will soon click on the provided link, navigate the fraudulent site, and disclose crucial private information such as your login credentials or other information. When they succeed in their attack, they may either use the information against you directly (for example, attempting to perform banking transactions with credentials you have revealed), or they may sell the information on the dark web to other cyber criminals. Or worse, both.
Protecting Your Company
When your employees need a second opinion about an email that they aren't sure is legitimate, it's important to provide a low friction way for them to get that second opinion without feeling that they need to file an IT helpdesk ticket or guess which colleague might have an opinion. A great way to offer a second opinion is by giving your employees access to the Mail Armor benefit in the Havoc Shield platform. It's easy to get started with Havoc Shield, using our Rapid Threat Test!
Interested in more articles about phishing? Continue here:
Any additional suggestions for article topics about phishing? Drop us a note in the comments section below!