Look-a-like domains have been a part of the threat landscape since at least 2001 (history), and although the nature of the associated attacks has evolved over the years, they all stem from one core premise. Cyber criminals using this technique as part of an attack are relying on the possibility that you might click on their fraudulent link with the belief that it leads to the website of a legitimate business entity that you know and trust.
Look-a-like domains use techniques such as omitting, replacing, repeating, or transposing characters from the legitimate domain name, to create a variant that closely resembles the original. Worse, IDN homograph attacks that use cyrillic letters brought about a set of domain names that are almost indistinguishable from their legitimate counterparts.
However, cyberattacks using look-a-like domains are getting a boost in effectiveness for an entirely different -- and mostly unanticipated -- reason. It's increasingly likely that you are reading their fraudulent email on your mobile device instead of your laptop or desktop, which could very possibly amplify the effectiveness of this attack vector. Read on to learn more.
Reading Email on Mobile Devices
According to emailmonday.com, 41.9% of emails are read on mobile, which has now eclipsed webmail (39.9%) as the most popular email reading modality. Furthermore, according to campaignmonitor.com, recipients of email read 24% of their email between the hours of 6pm-11pm.
Said another way, there is a really good chance that a cyber criminal might be fortunate enough that you receive their email on your mobile device, in the evening. Do you tend to spend some of your evening hours in an environment that is less brightly lit than your daytime workspace? I do.
Catching You with Your Lights Down
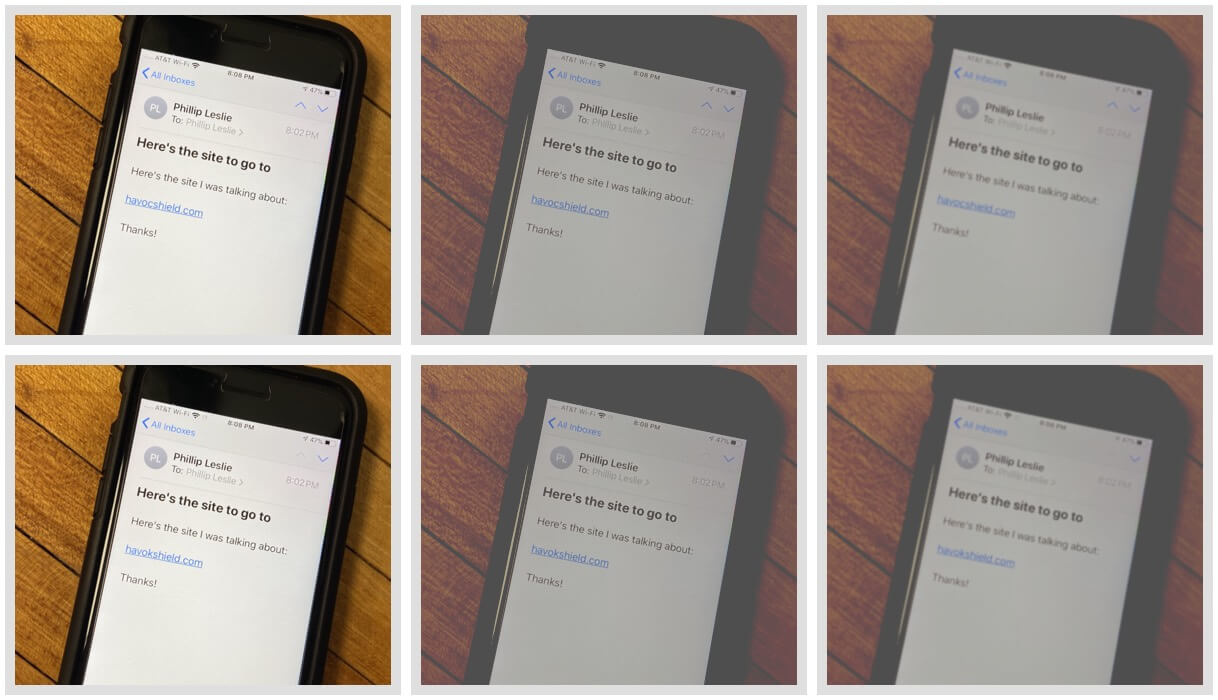
Suppose you received one of the following two emails and read them in a favorable lighting environment. No problem: I bet you can see which of the two emails points to our company's website. Depending on your vision, you might find yourself squinting a bit, but I bet you can pinpoint the correct vs the look-a-like:
Don't let that win build your confidence too high, though. What might it be like to try to discern legitimate from look-a-like in a less optimal lighting environment? Let's look:
Although your typical evening lighting environment may or may not resemble this one, it's hard to argue that your mobile device -- traveling with you most waking hours -- doesn't have you reading emails in a wide variety of lighting environments.
Finally, what if your vision isn't quite perfect? You know where this is headed.
The unfortunate truth is that cyber attackers using look-a-like domains already had the advantage: with bulk email attacks being cheap to send, and look-a-like domains easy to purchase, the effectiveness of phishing schemes continues to be amplified (unfortunately) by the additional deception of using call-to-action links that contain look-a-like domains. And, with the context of reading email on a mobile device, potentially in imperfect conditions, the odds for cyber criminals improve further.
Defending Your Threat Perimeter
If you own a domain and haven't looked at the look-a-like variants that could be (or may already be) registered, it's time to take a look. For variants that are not yet registered, the best practice is to purchase the domain name(s) and park them, so that they don't fall into the hands of cyber criminals. By registering the most compelling look-a-like domains, you limit the chance that a phishing attack could be effectively organized against the legitimate users of your website. It's a start. Want us to help you find, register, and park your domain's look-a-like variants? Hop into our Rapid Threat Test and we'll list out the ones worth registering -- and if you'd like, we'll do the heavy lifting on getting them registered for you.
Interested in more articles about phishing? Continue here:
Any additional suggestions for article topics about phishing? Drop us a note in the comments section below!