Before we dive into UNC Path Injection, let's talk about the good side of UNC paths. There is a lot to like about the UNC path system. Before the days of Google Drive, Box, Dropbox, etc., it was extremely common to share files within a company by letting other employees browse certain folders/files/resources hosted on your laptop/computer. Authenticated, usually. For example, I could have put an important PowerPoint presentation on my computer named PHIL-1, and made the file available to certain colleagues as \\PHIL-1\PRESENTATIONS\EXCELLENCE.PPTX -- and they would have readily been able to retrieve it.
Clickable UNC Paths
Extending the storyline, I might have emailed my colleagues with a message containing the UNC path in the body of the email. There is a very good chance that their email client would have turned it into a clickable link that would take them straight to the file. Easy. Tada! Having software that automatically turns UNC paths into clickable links sure is convenient!
But is it safe? What other files aside from PowerPoint presentations could someone share via a UNC Path?
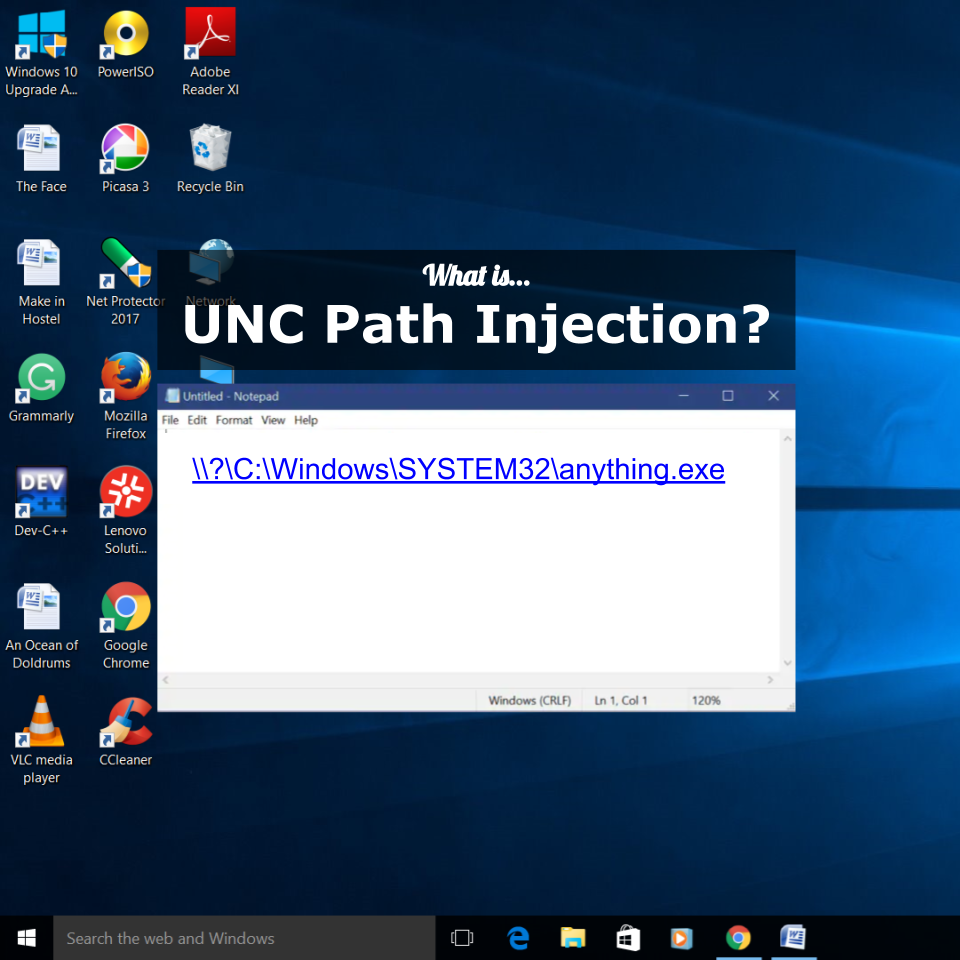
UNC Path Injection
A malicious actor (geek speak translation: cyber criminal) could take advantage of the fact that many software packages make UNC Paths clickable. Perhaps you can already imagine where this story goes next. What if a cyber criminal put a virus at a particular UNC path, or discovered a way to cause some pre-installed application to misbehave, when launched via UNC path?
A cyber criminal with a cleverly constructed UNC path only needs to be clever enough to fool their victim into clicking a link. Game over. Exploit complete.
What if they can remotely (without any particular access to your computer), cause their malicious link to appear on your screen... like by relaying it in a shared chat session or in an accidentally externally-writable cloud document? Injecting an intentionally mischievous UNC path in that context, could mean that a hacker could take advantage of you and your computer without ever having to do the hard work of finding a way to access your computer through a more direct network attack.
Staying Safe
Software providers are getting better (slowly, and sometimes only after an incident) at determining situations where the risks outweigh the benefits, for automatically displaying UNC paths as clickable links. We need software providers to get more and more thoughtful about their approach in this regard. We also need end-users to be naturally suspicious of any UNC Path link that arrived from anything other than the most trustworthy of sources.