
Spear Phishing Training: Advanced Tuning & Targeting
December 17, 2020
Phishing
Spear phishing training is an effort to fend off the most devious form of phishing: spear phishing. Spear phishing is a phishing attack that is targeted at an individual. Not a phishing attack claiming to be from Citibank sent to a million random recipients on the hope that some of them are Citibank customers. Not a phishing attack claiming to be package delivery information from UPS sent to hundreds of thousands of email addresses. A phishing attack whose message body is unique to one person, containing context relevant to that one person.
A few years ago this type of attack was talked about but not frequently seen in the wild: now it's seen by most of our clients, most months, but with some predictable patterns worth addressing via training. This post is our first shot at describing what we think that training looks like.
Spear Phishing Examples
We're going to need some examples to work with in the remainder of this article -- we're not writing an academic textbook here, we're writing about real spear phishing attacks that we commonly see "in the wild" in current times. Here are some of the most frequent ones:
- Gift Card Scam: a spear phishing attack where the attacker claims to be your CEO (by name), and sends you (an employee that is perhaps a few clicks down from the CEO on the org chart) an urgent request to purchase gift cards for a client gift. This spear phishing attack almost always comes with a warning that tells the recipient that the sender (supposedly the CEO) cannot be reached due to some critical meeting that can't be interrupted. And that the task needs to get done with no further clarifications or questions. What makes this spear phishing: this attack is frequently seen with correct/factual context of the CEO's name, the employee's name, and a target selection that makes it clear that the attacker chose an employee who is sufficiently junior as to be potentially intimidated by receiving instructions directly from the CEO. That's much more targetted than a bulk phishing attack.
- ACH Change for Accounts Payable: the spear phishing version of this attack involves an attacker who knows that there is a business relationship between two particular companies, and knows the name and email address of the person on the "buying" side of that business relationship. The person that will eventually be paying an invoice to the seller. This spear phishing attack involves someone posing as the seller, emailing the Accounts Payable person at the buyer's company, to inform him/her that the seller's ACH (banking) information has changed. And, that payment should now be routed to some revised destination. What makes this spear phishing: the attacker knows (or has very good reason to believe) that two particular companies have a billing relationship. The attacker knows (or has very good reason to believe) that they know which company pays the other. And, lastly, the attacker knows basic contact information about the Accounts Payable person at the buyer company.
- Payroll Changeover Phishing: if you've worked in a professional environment for more than a few years, there is a good chance that sometime during that span you've been through a transition where your company changes it's payroll system in a way that causes you to need to re-enter some information -- maybe even banking information -- in a new/revised system. It's sufficiently common that it's not a shock when it happens. And unless you are an exceptionally detail-oriented employee, it's probably hard to remember the particulars of the name and domain name of the "new" payroll system that you heard about in a companywide memo. So, when a well-timed spear phishing attack arises that asks you to complete your profile in a new payroll system -- that doesn't feel so unusual if you've recently been informed by HR that your payroll system will be transitioning. But it could be a financially disastrous mistake if it turns out to be a spear phishing attack instead of the legitimate message/site. What makes this spear phishing: if the attack is correctly and intentionally timed to take advantage of some known payroll transition occurring inside the company, its spear phishing.
Although there are many other examples of spear phishing, these three are each very common, and spear phishing attackers have developed incredibly clever ways to gather the necessary contextual cues to know when and how to stage their attack. And it's no accident at all, when they target YOU.
Phishing Training Is a Great Starting Point
Before we get into the particulars about setting up training specific to spear phishing, let's start with a recap on what a great phishing training sequence is. We'll add the "spear phishing" twist on top of the phishing training baseline. Here's an excellent phishing training sequence:
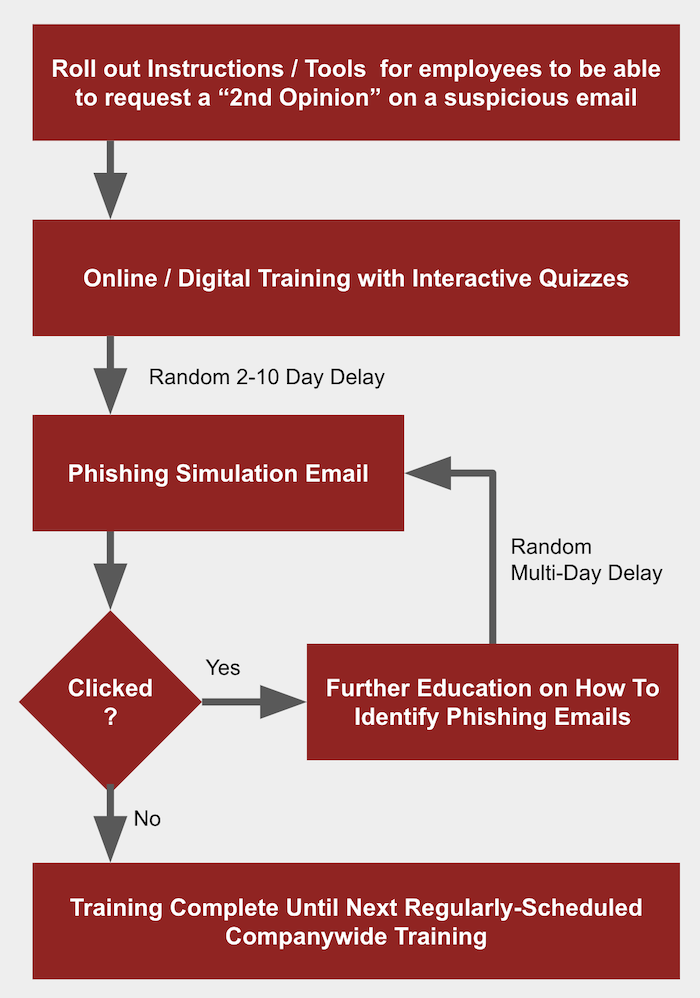
Let's walk through this briefly (this phishing training sequence) before we advance to the customizations unique to spear phishing training. In the above sequence, notice that it starts out with equipping employees with a "2nd Opinion" process. That's basically a route for employees to take if they ever receive an email that they think is suspicious. Maybe your company asks employees to forward suspicious emails to IT for a 2nd opinion. Maybe your company asks employees to send suspicious emails along to Havoc Shield's Mail Armor for a 2nd opinion. Whatever the process, having a 2nd opinion process/tool/mechanism is a vital aspect of having a credible phishing training program. It's what makes your employees feel "safe" about resolving uncertainty when an email seems unusual but not necessarily fraudulent.
Next, some online / on-demand training is in order. This doesn't need to be painful or time consuming. Just an online / digital training session that defines phishing, spear phishing, and related attacks, and has some basic quiz along the way. If you don't have something at-the-ready, just sign up for the Havoc Shield 14-day trial and roll out security awareness training to your team... that's a pretty good start.
Lastly, roll out randomized phishing simulation emails, and route any clicks to additional educational material before recycling the team back into another phishing simulation exercise until clicks dwindle to zero.
Spear Phishing Training: Advanced Tuning & Targeting
Finally, the advice that you've read this far to learn. How can a phishing training approach, like the one shown in the prior section, be adapted to be helpful for spear phishing training? Here are the key tuning and targeting decisions that we think you should most strongly consider:
- Hiring & Role-Change Triggers: thanks to the prevelance of social networks, it's becoming increasingly easy for spear phishing attackers to know when an employee is new to the company or has just changed roles. Those employees are at very high risk for spear phishing, because fraud like the gift card scam is uniquely effective against new-hires and role-changers. Consider conducting phishing training (perhaps with some of additional tweaks we'll describe next) with employees right when they are hired or right when they change roles.
- Custom Templates: any credible phishing simulation provider (certainly Havoc Shield) should be glad to offer customized templates that are tuned to your organization. Check out the formatting and style of your CEO's last companywide memo, and adapt the greeting, content style, and footer into a spear phishing template that asks employees to take some particular action, and incorporate the template into your phishing simulation. Make the requested action something that would never be authorized / acceptable.
- Establish "Never" and "Always" Norms: should accounts payable employees update ACH information after email-based instructions, with no further verification? Never. Will employees ever be asked via email by the CEO to purchase some reimburseable item? Never. Should employees being asked to enter their ACH information somewhere ask their HR person in a forum other than email if the request is legitimate? Always.. Establishing these norms, and including it in your rollout of spear phishing training, frees employees from the burden that spear phishing attackers hope to put on your employees. They hope to put your employees in a high-pressure time-sensitive situation where they feel like they must take autonomous action without any verification. Avoid that pressure, by preemptively setting expectations that rule out some of the most common frauds.
These three tuning and targeting techniques are some the easiest and most effective ways to adapt a phishing training strategy to be powerful as a spear phishing training strategy. If you lack any of the tools needed to execute on this advice, or simply want an ally to take some of the weight off of your shoulders, please be in touch and we'll be glad to help.